As the risk of cyberattacks increases, the European Union is strengthening IT security for financial companies such as banks, insurance companies and investment companies.
The European Union adopted the Digital Operational Resilience Act (DORA), which aims to revolutionize Europe's financial sector by improving operational resilience and streamlining legislation around digital operational processes.
Operational resilience encompasses a system's capacity to withstand losses and disruptions, as well as its ability to recover from them. In the realm of banking, insurance, and other financial services, it also pertains to an organization's capability to deliver critical services in the face of significant disruptions.
The importance of digital operational resilience has grown due to the rapid expansion of digital services, particularly the reliance on third-party technologies such as cloud infrastructure providers. This trend has been further accelerated by the COVID-19 pandemic. Regulatory authorities in Europe, the Middle East, and Africa have recognized the need for enhanced governance and controls in response to this shift, leading to the emergence of a global focus on digital operational resiliency.
DORA is a notable legislation that addresses the reliance of financial institutions on major cloud providers which aims to minimize the dangers linked to digital transformation by establishing standardized regulations on operational resilience across the European Union. This initiative has been launched to achieve the following objectives:
- Alleviate the risks arising from the expanding vulnerabilities caused by the growing interconnectedness of the financial sector.
- Tackle the changing risk landscape resulting from the widespread adoption of digital financial services.
- Recognize and address the reliance on third-party entities that underpin the stability of the financial sector.
- Implement a unified and consistent supervisory approach to operational resilience across the entire single market.
This will ensure that Europe's financial sector remains resilient in the face of major disruptions since DORA points to blend existing regulations, data, communication technology (ICT) and innovation risk policies da into comprehensive risk administration and management, and increment straightforwardness in dealings with ICT third-party suppliers. This point of interest control, pertinent to for all intents and purposes all money related substances in Europe, is set to bring around critical changes in inside operations, requiring key commerce choices, overhauled operational and ICT setups, and expanded preparing and upskilling endeavours.
A key highlight of DORA is its extra-territorial reach, requiring substances exterior the EU that give ICT administrations to comply with its arrangements in the event that serving monetary substances inside the EU. With the compliance due date set for the starting of 2025, budgetary substances confront a race against time, provoking critical activity from the financial sector and along with all parties involved. Further to whom DORA applies can be found below:
-Credit Institutions
–Payment Institutions
–Electronic Money Institutions
–Investment firms
–Crypto-asset service providers
–Central securities depositories
|
–Data reporting service providers
–Insurance and reinsurance
–Credit rating agencies
–Crowdfunding services providers
–Securitization repositories
–ICT third-party services providers
|
5-Core requirements of DORA
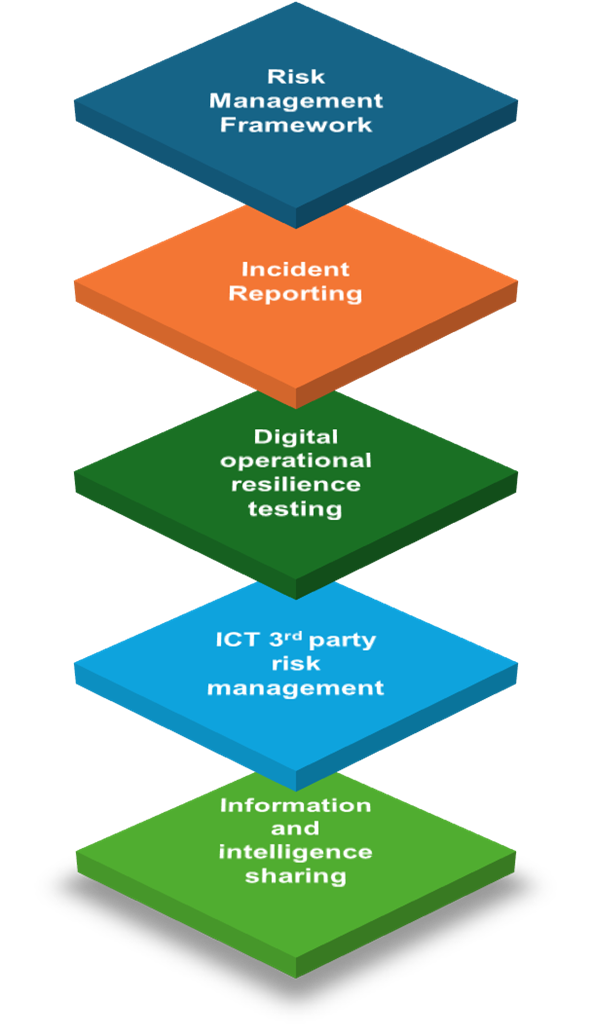
A set of specifications for the 5-cores can be found below:
Risk Management Framework
- Reduce the impact of ICT risk by establishing and maintaining robust ICT tools and systems.
- Continuous identification of all ICT risk sources is necessary to provide safeguards and preventative measures.
- It should be established to detect unusual behaviors promptly.
- In order to guarantee a speedy recovery from an ICT-related occurrence, thorough and committed business continuity strategies as well as disaster and recovery plans should be in place.
- Provide systems for the organization to grow and learn from both outside events and internal ICT mishaps.
Incident Reporting
- Create a management procedure and put it into action to keep an eye on and record issues involving ICT.
- Categorize the incident using the standards that are specified in the regulation and further refined by the ESAs, such as ESMA, EBA, and EIOPA.
- Ensuring that incidents are reported to the appropriate authorities according to a standardized process and template set by the relevant supervisory authority.
- Report ICT-related incidents to the firm's clients and users at the beginning, middle, and end.
Digital Operational resilience testing
- The readiness of the various components of the ICT risk management system should be checked on a regular basis.
- Any flaws, shortcomings, or holes must be noted and immediately fixed, either by implementing preventative measures or by mitigating their effects.
- The criteria for digital operational resilience testing must be commensurate with the size, type of business, and risk profile of the entities.
- To address higher degrees of risk exposure, conduct Red/Purple Team Assessments, commonly known as Threat Led Penetration Testing (TLTP).
ICT 3rd party risk
- Make sure you keep a close eye on any risks arising from depending on outside ICT providers.
- Coordinating essential service components and relationships with ICT third-party suppliers to allow for "full" monitoring.
- Make sure that all the monitoring and accessibility information, including a complete service level description and the locations where data is handled, is included in the contracts with the ICT third-party providers.
- Assist with the unification of supervisory strategies for ICT third-party risks by imposing a Union Oversight Framework on service providers.
Information Sharing
- The rules promote cooperation between reliable networks of different financial institutions. This partnership will improve:
- financial institutions' digital operational resilience
- increase knowledge of ICT hazards
- reduce the potential for ICT threats to proliferate
- assist organizations in their defence and detection methods, mitigation plans, or stages of response and recovery.
- Financial institutions are encouraged to share intelligence and information about cyber threats with one another by means of agreements that safeguard the potentially sensitive nature of the shared data.
DORA requirements are enforceable 24 months after entry into force (16th January 2023). Therefore, financial entities will be expected to be compliant with DORA by 17th January 2025.
Technology solutions that will help financial institutions to get under the DORA 5-core requirements umbrella
- IBM QRadar
- IBM Turbonomic
- IBM Instana
- IBM Cloud
- IBM Support Insights
- IBM Storage Defender (Cohesity DataProtect)
- Red Hat Enterprise Linux
- Red Hat Ansible Automation Platform
- Red Hat OpenShift Container Platform
- Red Hat Advanced Cluster Management for Kubernetes
- Red Hat Advanced Cluster Security for Kubernetes
- Red Hat Quay
- Checkpoint Endpoint Security
- Checkpoint Multi-Cloud Security
- Checkpoint Endpoint Detection & Response
- Checkpoint Managed Detection & Response
- GFI Languard
- GFI Mail Essentials
- GFI Faxmaker
- GFI Archiver
- Elastic Enterprise Search
- Elastic Observability
- Elastic Security
|
- Barracuda Firewall
- Barracuda Spam & Virus Firewall
- Barracuda Web Application Firewall
- Barracuda Web Security Gateway
- Barracuda SecureEdge
- Acronis Cyber Protect Cloud
- Acronis Managed Detection & Response
- Acronis Endpoint Detection & Response
- ESET Protect
- ESET Managed Detection & Response
- ESET Endpoint Detection & Response
- ESET Endpoint Antivirus
- ESET Endpoint Security
- ESET Full Disk Encryption
- Safetica Data Loss Prevention
|
About ZEBRA
ZEBRA Consultants is an innovative IT company that specializes in software development, infrastructure solutions, consulting services, systems integration and cloud solutions. Our expertise, coupled with our customer driven focus, allow our clients to tackle their technological challenges, boosting up competitiveness and maximizing their potential. Contact us sales@zebrac.com. Learn more at www.zebrac.com.